Review: HP WebInspect 10.20 Protects the Enterprise
Continuous diagnostics and mitigation (CDM) is the phrase of the day at federal agencies. At a time when zero-day attacks and previously unknown vulnerabilities can cripple an entire enterprise, knowing — in real time — what web applications exist on a network and the security holes they present is of paramount importance.
To that end, the General Services Administration and the Department of Homeland Security offer agencies access to CDM products through a blanket purchase agreement. One of those products is HP WebInspect.
WebInspect 10.20 is a powerful CDM tool. The program acts like a skeleton key, launching 3,300 bleeding-edge and updated attacks against web systems and then recording and reporting back each time an attack gets through. Obtaining a license to use it requires that a specific IP address range be preconfigured to be the target of its scans, though authorized users can add more addresses after the initial purchase by modifying their permissions.
WebInspect gives security professionals the ability to diagnose successful, hypothetical attacks against their web applications and services and plug holes to block a real hacker.
WebInspect supports Java and .NET applications. It works enterprisewide without regard to device, OS or existing security and returns a report so security professionals can identify vulnerabilities. The software flags false positives to create an exclusion list for future scans
For our review, HP set up a fake online bank so we could initiate scans and generate real reports. The software itself doesn’t require any special installation; a standard PC will do just fine, though a dedicated workstation or server would ikely yield results more quickly.
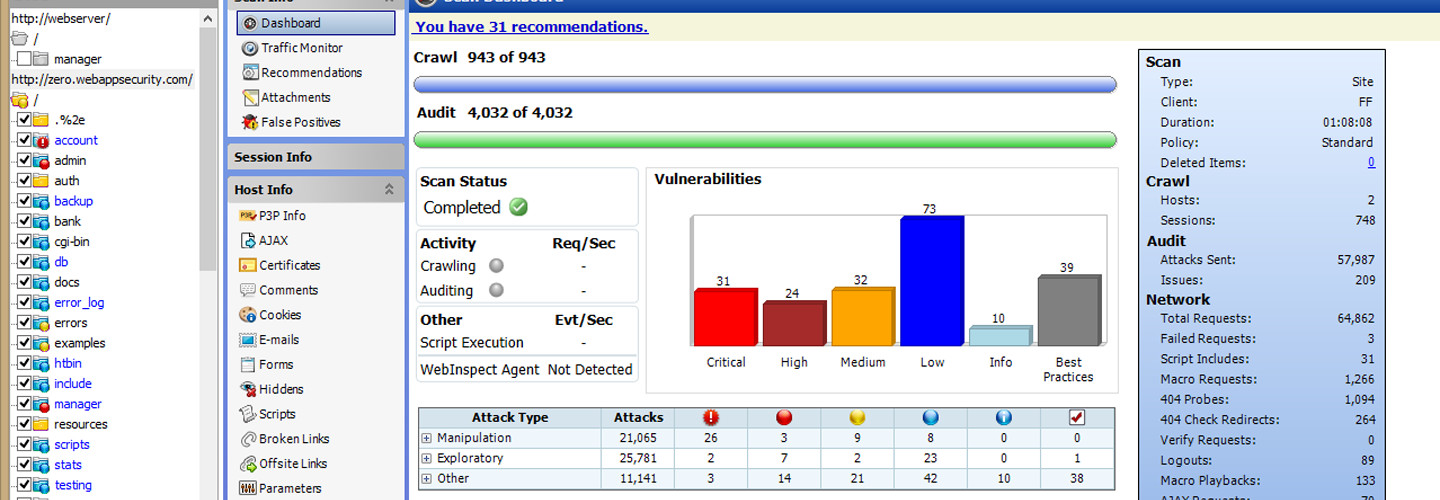
A full scan of 800 entry points took about a minute. Once complete, all vulnerabilities were grouped into classifications based on severity. We could then drill down into each to learn things like the names and locations of vulnerable devices, the attack path and exploit used, and the actual program or code that launched the attack.
Once a vulnerability is fixed, a security officer can rerun just the attack that worked against the now-patched device to ensure the hole is plugged. In this way, smart use of HP WebInspect can bring an enterprise into compliance one system at a time, while continuously scanning for new vulnerabilities that crop up
HP WebInspect 10.20
CPU: 1.5GHz single-core (minimum); 2.5GHz multi-core (recommended)
RAM: 2GB (minimum); 4GB (recommended)
DISK: 40GB (minimum); 100GB+ (recommended)
OS: Windows 7 (32- or 64-bit) with SP1 (recommended); Windows 8; Windows Server 2008 R2 (64-bit) with SP1; Windows Server 2012