Review: Carbon Black Cb Defense Goes Beyond Traditional Endpoint Protection
For years, the best tool to protect desktops or notebooks was signature-based anti-virus software, which saved and constantly updated records of all known malware patterns and generated an alert when a protected endpoint ran into anything rogue. Some traditional protection programs also added heuristics to look for known malware patterns.
Even today, a traditional anti-virus program with updated signatures and heuristics can likely protect against 90 percent or more of the most common threats. But the effectiveness of traditional anti-virus solutions is decreasing, and the most sophisticated attackers, such as those who target government agencies, know how to get around signature-based protection.
In response to that evolving threat landscape, Carbon Black has adjusted the focus of endpoint protection and dropped signatures altogether. Cb Defense concentrates on the system itself, including the numerous processes a protected computer uses to operate every day. Each is examined algorithmically, which enables the solution to identify malicious activity, regardless of how the malware is deployed.
Government IT Admins Can Deploy Cloud-Based Security
Using Cb Defense in an enterprise environment is simple. Users manage the entire program centrally through the cloud. As long as an administrator has access permissions on endpoints, the solution will push out small, lightweight agents to every Microsoft Windows–based computer within the environment. Those agents don’t affect system performance.
In my testing, systems with agents installed performed identically to those without. Each studies the system it is charged with protecting, learning about the programs and processes used every day, and ranking them with algorithm-based logic.
For enterprise customers, should the program flag a threat that admins can’t fix, Carbon Black offers tech support via phone, email or a web-based interface and guarantees a response to critical problems within a few hours.
The changing nature of attacks on endpoints requires a new approach to defense, especially for government organizations, which are tempting targets for professional attackers.
Cb Defense can provide that protection, regardless of how or what type of malware is used in an attack.
Feds Can Guard Against Advanced Persistent Threats
By far the most dangerous type of cyberattack — one that has produced some alarming security breaches — is the advanced persistent threat.
Unlike malware that is released into the wild, APTs generally are carefully deployed and monitored by cyberattackers who are trying to crack a specific organization’s defenses.
Attackers working with APTs take note every time an attack fails. They then study the reasons for the failure, change a few parameters and try again.
Often operating from offshore safe havens in countries that do not prosecute cybercrimes — or sometimes directly supported by a rogue government — they have time to try, and try again, to break into a targeted organization. Most of the time, they know what they want to steal, whether the target is users’ or constituents’ personal or financial information, or data such as passwords for financial accounts.
Even if a defensive tool is able to stop an APT attack, if that’s all it does, then it’s simply providing more information for the attacker. The best defenses must capture as much information about the tools, targets and tactics of attackers so that organizations know that they are under attack and can plan their defenses.
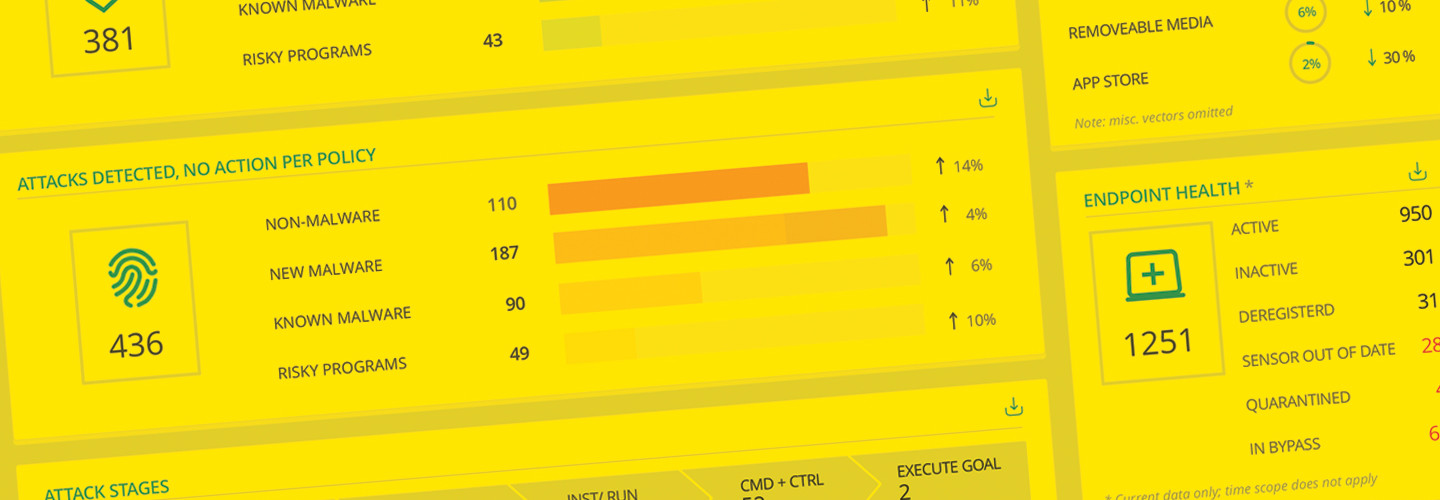
Cb Defense from Carbon Black does just that. After each attack on a test network protected by Cb Defense agents, the central management console provided a wealth of information about the attacker. This included the tactics that were being used, the location of command and control servers, the targets the malware was trying to compromise and what, if any, information was delivered to the attacker.
The Cb Defense reports contain a wealth of information that is essential to threat hunting, to see if defenses have been breached anywhere else. In testing, the reports revealed particularly weak pathways in the test bed, as well as the location of the data the malware was trying to access.
All of this information could be used to improve network defenses, or even to write specific rules for other security programs to automatically counter attackers, even if they find a way to bypass the endpoints.
This capability makes Cb Defense a particularly powerful security solution. It can protect endpoints from attacks — even the most advanced, previously unknown exploits — almost completely, while also providing a wealth of information and threat intelligence that can be used to better protect both endpoints and core assets in the future.
The Carbon Black Cb Defense
Agents Per Endpoint: 1
Max Agents: Unlimited
Endpoint OS: Windows
License: 3 years
Availability: 24/7 by phone, email or web
Response Time: 4 business hours