WannaCry Ransomware Attack Linked to North Korea, Cybersecurity Experts Say
The WannaCry ransomware attack that started Friday and infected hundreds of thousands of computers has been linked to hackers aligned with North Korea, according to cybersecurity researchers. However, the evidence is not conclusive.
Moreover, the malware code used in the attack has its origins in a cyberweapon that was stolen last summer from the National Security Agency by a mysterious group calling itself the “Shadow Brokers.” The hack highlighted the vulnerability the spy agency faces, despite spending hundreds of millions of dollars to ramp up its own cybersecurity since former NSA contractor Edward Snowden disclosed internal agency files on its eavesdropping programs in 2013.
In the wake of the attack, which also goes by the name WannaCrypt, a top executive at Microsoft criticized the government for stockpiling software vulnerabilities and keeping them secret. Brad Smith, Microsoft’s chief counsel, said Sunday in a company blog post that the practice of hoarding so-called zero-day exploits (so called because it’s not publicly reported or announced before it is used) leads to attacks like WannaCry.
The North Korean WannaCry Connection
Cybersecurity experts say there is circumstantial evidence that links the WannaCry attack, which started Friday in Europe and then spread around the globe, to cyberattacks previously tied to North Korea.
Security experts at Symantec, which in the past has accurately identified attacks mounted by the United States, Israel and North Korea, found early versions of the ransomware, called WannaCry, that used tools that were also deployed against Sony Pictures Entertainment, the Bangladesh central bank last year and Polish banks in February. American officials said Monday that they had seen the same similarities.
The WannaCry attack “bore some striking similarities to the code used in those three attacks. That code has not been widely used, and has been seen only in attacks by North Korean-linked hackers,” according to the Times. Moreover, in addition to Symantec, researchers at Google and Kaspersky Lab confirmed the coding similarities, the Times reports. Indeed, the Guardian reports that “the similarities were first spotted by Google security researcher Neal Mehta and echoed by other researchers including Matthieu Suiche from UAE-based Comae Technologies.”
Researchers are keen to point out that more investigation is needed before any definitive conclusions can be drawn. The Guardian notes: “Shared code doesn’t always mean the same hacking group is responsible – an entirely different group may have simply reused Lazarus group’s backdoor code from 2015 as a ‘false flag’ to confuse anyone trying to identify the perpetrator. However, the reused code appears to have been removed from later versions of WannaCry, which according to Kaspersky gives less weight to the false flag theory.”
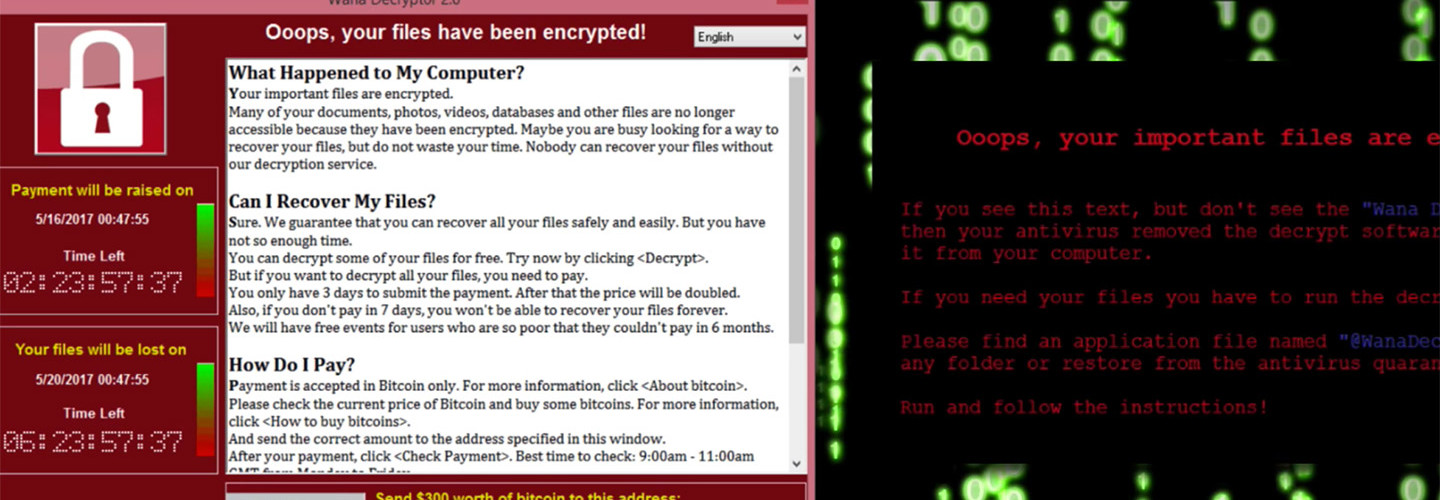
As of Sunday, the cyberattack had struck more than 200,000 computers in more than 150 countries, according to Rob Wainwright, the executive director of Europol, Europe’s police agency, the Times reports. The attack, which locked users out of their systems and networks and demanded ransom of about $300 in the form of Bitcoin digital currency, crippled hospitals, businesses and government agencies.
I will confess that I was unaware registering the domain would stop the malware until after i registered it, so initially it was accidental.
— MalwareTech (@MalwareTechBlog) May 13, 2017
There was no evidence on Monday of a second wave of attacks like the one that hit Friday, the BBC reports. Over the weekend, a 22-year-old cybersecurity researcher from England named Marcus Hutchins discovered and inadvertently activated a “kill switch” buried in the malware’s code. A new variant of the WannaCry attack surfaced on Monday, according to cybersecurity firm Check Point Software Technologies, but the firm stopped it by using the kill switch, Reuters reports.
Microsoft Takes Government Agencies to Task Over WannaCry
How did all of this get started? With the Shadow Brokers’ theft of the NSA’s cyberweapons.
As the Times reported after the first wave of attacks, WannaCry appears to be “the first time a cyberweapon developed by the NSA., funded by American taxpayers and stolen by an adversary had been unleashed by cybercriminals against patients, hospitals, businesses, governments and ordinary citizens.”
The U.S. government “has never confirmed that the tools posted by the Shadow Brokers belonged to the NSA or other intelligence agencies, but former intelligence officials have said that the tools appeared to come from the NSA’s ‘Tailored Access Operations’ unit, which infiltrates foreign computer networks. (The unit has since been renamed.),” according to the Times.
In his blog post, Microsoft’s Smith says that “the governments of the world should treat this attack as a wake-up call.” He says the attack “provides yet another example of why the stockpiling of vulnerabilities by governments is such a problem,” noting that, earlier this year, WikiLeaks posted vulnerabilities that had been stored by the Central Intelligence Agency. This is an emerging pattern in 2017.
“Repeatedly, exploits in the hands of governments have leaked into the public domain and caused widespread damage,” Smith says. “An equivalent scenario with conventional weapons would be the U.S. military having some of its Tomahawk missiles stolen. And this most recent attack represents a completely unintended but disconcerting link between the two most serious forms of cybersecurity threats in the world today – nation-state action and organized criminal action.”
Smith says cyberweapons require a new approach, and governments must “consider the damage to civilians that comes from hoarding these vulnerabilities and the use of these exploits.” He notes that in February Microsoft called for a new “Digital Geneva Convention” to address these issues, “including a new requirement for governments to report vulnerabilities to vendors, rather than stockpile, sell, or exploit them.”
In an effort to immunize users, Microsoft on Friday took the unusual step of issuing patches for customers running platforms that are no longer receiving regular security updates — Windows XP, Windows 8 and Windows Server 2003. In March, Microsoft released a security update for supported operating systems which addresses the vulnerability that WannaCry exploits.