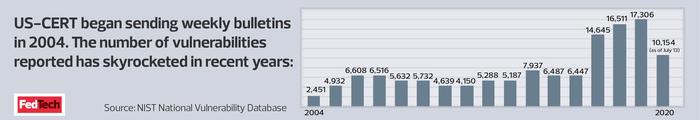
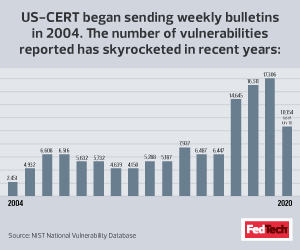
From minor vulnerabilities such as stored cross-site scripting that lets an attacker steal cookies to more major threats such as structured query language injections or foreign agents attacking networks, the U.S. Computer Emergency Readiness Team keeps IT professionals and the public informed of cyber dangers.
US-CERT, part of the Cybersecurity and Infrastructure Security Agency within the Department of Homeland Security, regularly releases five types of security content as part of the National Cyber Awareness System: bulletins, current activity, alerts, analysis reports and tips.
The tips are meant primarily for nonexpert end users; they provide easy-to-understand advice on identifying social engineering attacks, checking digital signatures, securing Wi-Fi networks and preventing malware infections.
The other categories are aimed at cybersecurity professionals and other technical personnel, and US-CERT regularly sends advisories that let this group know about cyber problems that must be resolved.
This content is intended to help federal agencies and others have better awareness and understanding of the latest cyberthreats and vulnerabilities so they can improve their defenses and prevent compromises. Each of the four technical content categories has its own value and its own best practices for federal agencies to follow if they want to use the content.
Alerts Help Agencies Respond to Cybersecurity Vulnerabilities
First are bulletins, also known as security bulletins, which list all vulnerabilities added to the National Institute of Standards and Technology’s National Vulnerability Database (NVD) in the past week. Agencies should review these for a snapshot of the previous week’s new vulnerabilities.
Vulnerabilities are grouped based on their severity — high, medium or low — and are listed within each group alphabetically by vendor and product name. Each entry contains basic information about the vulnerability as well as links to patching information, vendor bulletins and the related NVD entry. NVD grows by numerous vulnerabilities per day, so one weekly bulletin may have more than 100 entries.
Bulletins are probably most useful to an agency’s system administrators and vulnerability management personnel, who have the expertise to scan for new vulnerabilities that might affect them. NVD also offers more detailed, machine-readable data on vulnerabilities.
The current activity content appears several times per week, enabling IT staff to plan vulnerability remediation. These announcements are mostly brief descriptions of patches and other updates that eliminate vulnerabilities in widely used software, with pointers to vendor advisories and bulletins with more information.
In cases where updates aren’t available, current activity write-ups will have temporary work-arounds useful to system administrators and other personnel responsible for patch management.
Some current activity write-ups are announcements of security-related publications from other government agencies, both in the U.S. and elsewhere, and from information sharing and analysis centers. Those publications tend to cover topics including the latest social engineering attacks as well as other cyber scams.
Current activity write-ups on these topics may be of interest to a wider range of agency IT staff, such as help desk personnel and others who may field questions from users about suspicious requests they have received.
READ MORE: What are the fundamentals of zero-trust security?
Feds Get Short Bulletins on Emerging Threats
The alerts, also called technical alerts, contain information on emerging threats and vulnerabilities and appear a few times per month.
Some alerts contain information on campaigns by particular nation-states or hacker groups; others outline threat trends such as the use of topics related to COVID-19 in social engineering attacks. They also include advice on how to prepare for those threats. Each alert is about a page or two of text, a short read ideal for agency incident responders, vulnerability management personnel and others who need to learn quickly how the next attack may appear.
Finally, analysis reports come out once or twice a month and contain highly technical and detailed information on how to detect certain new malware threats. Most are labeled as “malware analysis reports” and are developed by several agencies working together.
For instance, in early May, DHS, the FBI and the Department of Defense released a MAR outlining the workings of three North Korean malware variants.
Intrusion detection specialists and incident response personnel may find these analysis reports to be particularly beneficial.
The reports on new malware provide them with details that can be added to detection technologies, searched for in security log files and used by other security controls to find and prevent the malware in an agency’s environment.
Among these details: precisely what the malware does (e.g., exfiltrate information); how to identify the malware files, such as cryptographic hashes, file names and file sizes; and how the malware behaves — for example, the names of processes it runs or the IP addresses or domains it contacts.
The reports also often link to indicators of compromise files, which basically document many of these signs of the malware in machine-readable formats.
This makes the information easily consumable by compatible security tools, which can ingest the threat intelligence information and use it to find any and all instances of that malware in that environment.