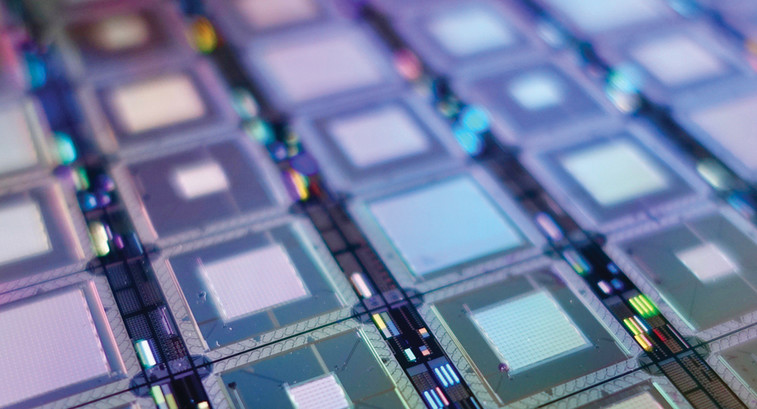
The Energy Department, NSF and NIST will work together to promote the radical technology, with additional backing from the White House.
Derek Rice
Close


New Workspace Modernization Research from CDW
See how IT leaders are tackling workspace modernization opportunities and challenges.
Copyright © 2026 CDW LLC 200 N. Milwaukee Avenue, Vernon Hills, IL 60061
Do Not Sell My Personal Information