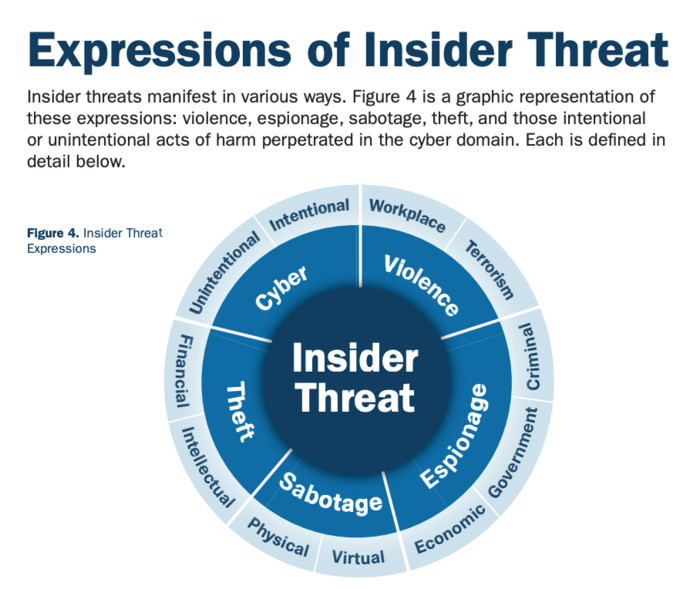
The Cybersecurity and Infrastructure Security Agency notes that insider threats can be expressed in several different ways. Source: CISA
For example, it might be a user in accounting who suddenly goes for the first time ever into the file directory that has top-secret information on an agency’s high-value assets, according to Kovar. Or, perhaps the information is not top-secret but is something that has nothing to do with the user’s normal work.
If there is a user who normally does interact with high-value assets and information, an unusual aspect or behavior might be that the IT security team has detected the user has downloaded the information to the desktop and put it on a USB drive for the first time.
This behavioral monitoring requires the agency to map out the baseline of normal behavior for users, Kovar notes.
“We can condense through peer group analysis, and say, ‘Hey, this person does this thing every single day. Why are they accessing these folders or this email directory for the first time ever?’” Kovar says.
Insiders are much more likely to use physical exfiltration, such a printing out documents, copying information on local hard drives and accessing data via USB drives and ZIP disks, Kovar says.
Other behavioral indicators of insider threats that CISA notes include “observable resentment with plans of retribution”; “excessive or unexplained use of data copy equipment (scanner, copy machine, cameras)”; “bringing personal equipment into high security areas”; “disgruntlement toward peers due to perceived injustice”; and “excessive volunteering that elevates access to sensitive systems, networks, facilities, people or data.”
Technical indicators of insider threats noted by CISA include email messages with abnormally large attachments or amounts of data, Domain Name System queries associated with dark web activities, the use of activity masking tools such as VPNs, connecting an unauthorized device to the network, downloading or installing prohibited software, unexpected activity outside of normal working hours and attempts to bypass or disable malware protection tools or security controls.
READ MORE: Learn why agencies should take a new approach to data security in 2021.
How to Create an Insider Threat Program
CISA lays out the ground rules for creating an effective insider threat mitigation program. They include the ability to identify and focus on “those critical assets, data, and services that the organization defines as valuable.”
The program must also monitor user behavior “to detect and identify trusted insiders who breach the organization’s trust.” Another key element is that the program “assesses threats to determine the individual level of risk of identified persons of concern.”
An effective program must also manage “the entire range of insider threats, including implementing strategies focused on the person of concern, potential victims, and/or parts of the organization vulnerable to or targeted by an insider threat.”
Solid programs, CISA states, must also “engage individual insiders who are potentially on the path to a hostile, negligent, or damaging act to deter, detect, and mitigate.”