There’s no such thing as a foolproof cybersecurity strategy. That’s why network visibility is so important.
“You can’t block all threats,” says Chris Butera, senior technical director for cybersecurity at the Cybersecurity and Infrastructure Security Agency. “Well-resourced adversaries are going to find a way to get an initial foothold.
“Network visibility is necessary for stakeholders to understand what’s happened on the network, as well as to support the successful eviction of a malicious actor.”
Cybersecurity, for obvious reasons, has always been a top-of-mind priority for federal agencies. But since the discovery of the SolarWinds attack late last year, the emphasis on security in federal IT environments has been perhaps even greater.
The attack compromised at least nine federal agencies, along with a 100 private enterprises, and underscored the need for constant vigilance.
At a press conference in February, federal officials cited the role of limited network visibility in agencies’ difficulties spotting and responding to the SolarWinds attack.
“Even within federal networks, culture and authorities inhibit visibility, which is something we need to address,” says Anne Neuberger, deputy national security adviser for cyber and emerging technology. “If you can’t see a network, you can’t defend a network. Federal networks’ cybersecurity environments need investment and more of an integrated approach to detect and block such threats.”
In May, the White House issued an executive order on improving the nation’s cybersecurity, outlining CISA’s role working with other agencies to protect them against cyberthreats.
Both CISA and agencies across government are implementing tools and best practices designed to bring additional visibility to federal IT networks.
“At CISA, we’re investing in and growing our capabilities to assess risk,” says Butera. “A lot of this work necessitates a fundamental change, where CISA can hunt for threats and conduct rapid analysis for both federal agencies and nonfederal organizations.
“With this increased visibility, we’re better able to identify adversarial activity across multiple agencies, and potentially critical infrastructure sectors as well.”
COMPLIMENTARY RESOURCES FROM CDW: Find out how to craft an effective cybersecurity incident response.
Network Visibility Tools and Best Practices Agencies Should Use
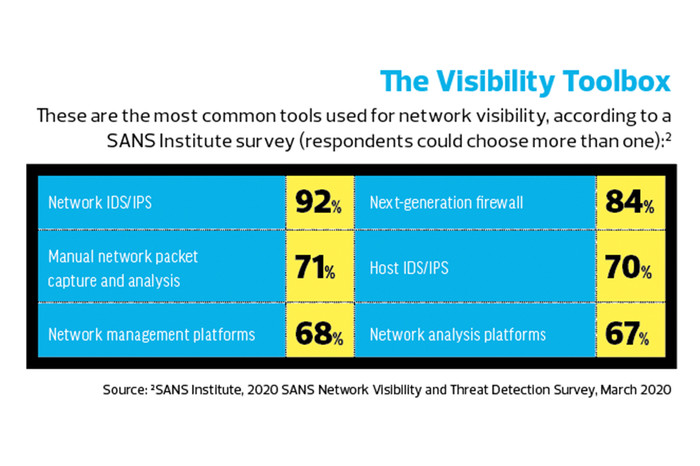
Network visibility requires a mix of tools and best practices designed to establish baselines for network traffic and spot anomalies. “Getting a holistic picture of activity on the wire and at the endpoint is needed to paint that realistic picture of what is happening across your network,” Butera says.
He highlights tools such as intrusion detection system, endpoint detection and response, security information and event management (SIEM) and vulnerability scanning tools.
These solutions, he adds, must be combined with best practices such as timely patching, comprehensive logging and building an asset inventory of what is present on a given network.
“One of the most important tools is identity and access management logging, which is really about understanding who is accessing your resources as well as who is performing administrative or privileged functions on your network,” Butera notes. “It’s important to have these records, not only for on-premises environments but also for the cloud.”
The Defense Information Systems Agency is beginning the process of identifying, characterizing and reporting all devices connected to the agency’s network. The effort is part of the Department of Defense Comply-to-Connect program, which specifies critical steps to defend organizations from cyberattacks and mitigate risk.
“The first step is identifying all of the devices that connect to your network, and then collecting data to automate and normalize what we see,” says Serena Chan, director of the Cyber Development Directorate at DISA. “Based on those findings, we can determine a state of compliance and also push out standards, policies, patching — all of those things to keep the network healthy.”
Kevin Bingham, zero-trust technical lead for the National Security Agency, notes that network visibility goes hand in hand with a zero-trust approach to network security, which grants no implicit trust to assets or user accounts based on location or ownership.
“We recommend zero trust because the classic perimeter cybersecurity strategy can only do so much against a well-resourced and determined adversary,” Bingham says. “The zero-trust model is a system of principles rather than a set of tools.
“It must be embraced by senior leadership, and it has to be carried out by network administrators so that they can tailor security to their own networks,” he adds.
While there is no single off-the-shelf product that can deliver zero trust, Bingham notes that agencies can chose from a number of tools that enable zero trust to include visibility of endpoints, cloud environments and network performance.
KEEP READING: Check out these complimentary resources from CDW for guidance on building an incident response plan.
Feds Look to Balance Automation and Human Cyber Responses
Colorado Army National Guard Lt. Col. Brad Rhodes — who, as a civilian, is the head of cybersecurity for a threat detection company — this year led the Guard’s most recent round of Cyber Shield exercises, designed to simulate real-world cyberattacks (in this case, an attack targeting networks tied to water infrastructure).
Rhodes highlights the delicate balance that agencies must strike between automating large portions of their cybersecurity actions and bringing in human expertise and manual efforts when needed.
“It’s definitely a balance,” Rhodes says. “You can certainly automate a lot. But you can do all the alerting you want, and if the threat actors out there have discovered a way around your alerting, then they’re on your network and you don’t have any alerts.”
Rhodes stresses the importance of SIEM systems, but also cautions that these tools must be finely tuned to avoid alert fatigue.
“If you don’t tune your SIEM, you get overloaded with alerts, and it just becomes noise,” he says. “People don’t pay attention anymore, and that’s not a good place to be.”
The National Guard follows National Institute of Standards and Technology guidelines on cybersecurity and network visibility, Rhodes says. However, he points out that there is no standard set of networking equipment used across government, meaning that the actual application of those standards is unique wherever the NIST guidelines are followed.
Besides, Rhodes notes, organizations need to not only inventory their IT assets but also establish baselines for how those assets are being used in order to lay a foundation for their network visibility efforts.
“You need to know what you have,” Rhodes says. “It’s the hardware, the software, the operating system, the accounts. It’s asking how many administrators do you have, where are your data stores? We’re putting more and more things on networks than we ever thought we would, and each one of those things increases our attack surface.
“You can take two organizations and give them the exact same tools and capabilities, and if I were to look at the traffic on both networks, they would look drastically different, because of the human element.”
Agencies Seek to Unify Government Cybersecurity Efforts
The NSA’s Bingham notes that while the agency has been advocating for a voluntary move to zero trust for some time, the May executive order now directs agencies to move to cloud and zero-trust architectures — and to modernize security accordingly.
“That’s the direction we need to go,” Bingham says. “Another aspect of the executive order is that it serves to drive unity of efforts across the government to defend vital systems and data.”
Last year, he says, NSA stood up the Cybersecurity Collaboration Center to create a forum where National Security System owners and Defense stakeholders and partners could engage with NSA and each other to discuss guidance and best practices.
“The executive order is another step in the right direction to achieve that unity of effort that will better protect our critical networks,” he says.
The White House’s executive order details a number of steps for CISA to take to help improve network visibility and overall cybersecurity across government.
Among them: CISA will work with the Office of Management and Budget to recommend contract language that makes it easier to share critical data, support efforts to promote visibility and incident response in cloud environments and help develop procedures for ensuring that cyber incident reports are shared quickly across government.
CISA also supported OMB in developing a policy to require logging, log retention and log management in all federal agencies to improve visibility across the federal landscape.
“We have a multipronged approach — providing tools directly to agencies, and also providing cyber services and guidance,” says Butera. “Although the initial EO tasks are wrapped up, we have years of work ahead.”
EXPLORE: How are federal agencies evolving their approach to cybersecurity?