Symantec Advanced Threat Protection: Network - An Innovative CyberDefense Tool
Following a series of high-profile attacks against its networks, the federal government has worked to bolster its cybersecurity defenses. Perhaps most notably, the Department of Homeland Security has upgraded its EINSTEIN program, which adds endpoint security and protects notebooks, tablets and phones connected to government networks. But EINSTEIN is not yet available to all contractors and is mostly a traffic signature–based program.
Enter Symantec’s Advanced Threat Protection: Network. This program is an innovative defense tool that makes use of machine learning to quickly detect and remedy threats against endpoints. Symantec has deployed over 175 million endpoint agents around the world, with each reporting the suspicious behaviors and possible threats it encounters back to headquarters.
Shoring Up Cyberdefenses
For our testing, we set up a network of virtual machines to simulate a production environment of Windows, Mac and Linux clients, all of which the program supports. By deploying one agent, and by taking advantage of wizard-enabled machine learning, the program can exploit endpoint detection and response technology and anti-malware for each client.
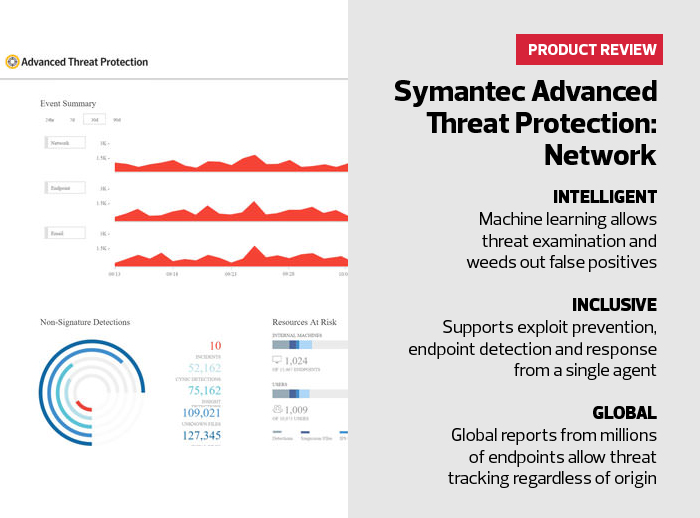
The protection proved to be lightweight, allowing quick scans from the central console; each agent continued to work whether or not an operator watched. Once deployed, I used the dashboard to view a list of threats lurking in our test network.
Machine learning helped eliminate false positives. The program caught all the malware I injected into the endpoints, including more advanced stealth tools. In addition, the software showed its work, highlighting all files used in an attack, as well as email addresses, lateral movement and malicious IP addresses involved from the outside. The software is easy to use. I could remove suspect files and block threat venues with a single click. The product also integrates seamlessly with software from analytics provider Splunk and cloud company ServiceNow. Federal agencies that require multiple layers of defense could shore up their defenses in a relatively painless deployment using Symantec’s Advanced Threat Protection.
Can All Protection Software Get Along?
One major problem with relying on a single cybersecurity vendor is that when an attacker learns there is just one obstacle to overcome, it can work to circumvent that particular protection. Layering multiple programs within a network solves the problem of keeping all of your eggs in one basket, but the implementation often proves more difficult than it seems.
Agents, those tiny little programs that enable the main consoles to function, often behave like malware, silently reporting what they find back to a central server. That can trigger other security programs to flag them as malware, starting a tit-for-tat war, where the only winners are attackers who can make use of that chaos. As such, the new trend is for cybersecurity programs to try to get along.
Symantec’s Advanced Threat Protection is designed to deploy agents and provide its protection without interfering with any existing defenses. We tested that by deploying McAfee endpoint protection and Malwarebytes anti-malware on several virtual clients in our test bed before adding the Symantec protection agents. Surprisingly, the presence of multiple defenses did not immediately trigger a storm of false positives or internal warfare. But the true test came when we injected advanced malware into multiple protected endpoints.
It passed.
The only setback occurred because the programs seemed to compete to identify and remediate the threat first. The Symantec program, which won that three-way skirmish about 50 percent of the time, would identify the threat and report it to the main console as normal — if it grabbed the intruder first. When another program found and quarantined or eliminated the threat, the main Symantec console would not generate a report because the agent technically never saw it.
That scenario probably won’t prove to be a problem for most admins, but, if that’s a concern, they should check program logs from time to time in order to see which low-level threats were automatically eliminated and by which protection.
The good news for all admins is that today’s cybersecurity programs, including Symantec’s Advanced Threat Protection, seem to be more willing to work together than in the past. Healthy competition exists, but the benefit goes to the networks being protected, not some outside threat looking to take advantage of internal fighting.