It’s also important to weigh the advantages of going the SECaaS route against the possible drawbacks of doing so. Agencies that rely on SECaaS often reduce their overall security costs, and they typically benefit from cutting-edge tools designed to address emerging cyberthreats, for example. At the same time, agencies should take care when finalizing their SECaaS contracts.
“Just because something is ‘security software’ doesn’t mean it’s secure software,” Yasar says. “It’s the same thing with SECaaS: It’s up to you to make sure that the solution you’re getting has everything you need and is really secure.”
Former CIA CISO Robert Bigman says that just because a service is listed in FedRAMP doesn’t mean it’s the right fit for a specific agency.
“Proceed with caution,” he says. “FedRAMP authorization is a good first step, but remember that the devil is in the details.” He recommends determining total cost of operation for on-prem ownership for any security products, then carefully comparing that figure with the costs associated with various SECaaS offerings.
WATCH: These are the five IAM trends to monitor in 2026.
If a service solution seems financially beneficial, it should then fall to the agency’s CISO (or their representatives) to ensure that any contracts spell out exactly what the organization expects.
“It can’t just be your CFO who’s involved; it has to be someone who knows what you already have and the specific settings you want the CSP to use,” Bigman says. In his experience consulting with organizations in the financial sector, the companies that got the most out of their SECaaS deployments were those that weren’t afraid to be demanding. “They dictated the measures of performance and they documented everything,” he says.
SECaaS Is a “Necessity”
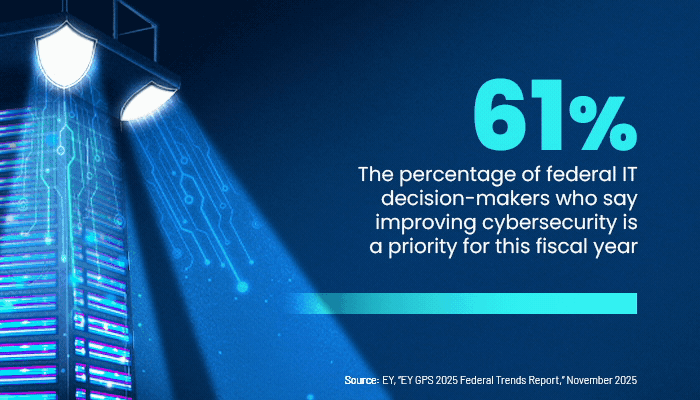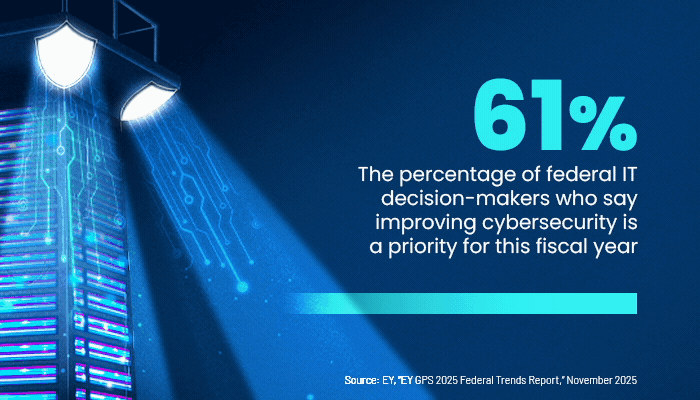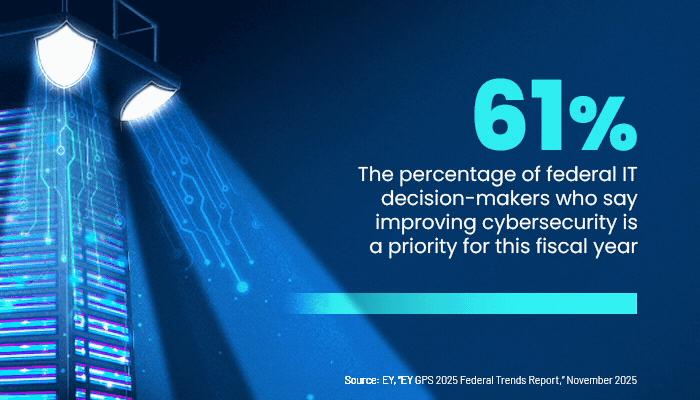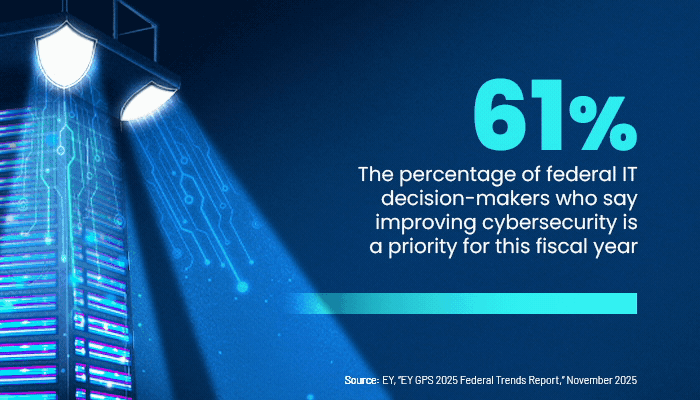
Larry Hughes, vice president of research and development at the Cloud Security Alliance, says that improving an organization’s cybersecurity performance is what SECaaS is all about. Especially as federal IT employees are furloughed or choose to leave government for jobs in the private sector, such services are increasingly becoming a “necessity” for agencies, he says.
With SECaaS, historically manual tasks such as real-time monitoring of networks and systems to detect and respond to security threats suddenly become much more manageable. “The CSPs are experts at this, and they can do it at scale and be highly cost-effective,” Hughes says.
UP NEXT: Agencies handling genomic data need identity-focused access governance.
Previously a security-compliance consultant, Hughes has more than a decade of experience helping companies in the private sector understand and meet federal government security requirements. SECaaS providers are constantly updating their offerings as the threat landscape evolves, and he points to a variety of technologies when asked to predict the future of the FedRAMP marketplace.
“Artificial intelligence and zero trust are obviously becoming more important, and I think that developments in quantum-resistant cryptography aren’t far behind,” Hughes says.
His advice to federal agencies aligns with that of other security experts: SECaaS “isn’t the answer to everything,” but it can be a tool in the federal cybersecurity kit.